How To Crack Roboform Master Password Reset
I screwed up trying to change my master password. Now all of the entries say the password (I try the new one, then the old one) say it is wrong.
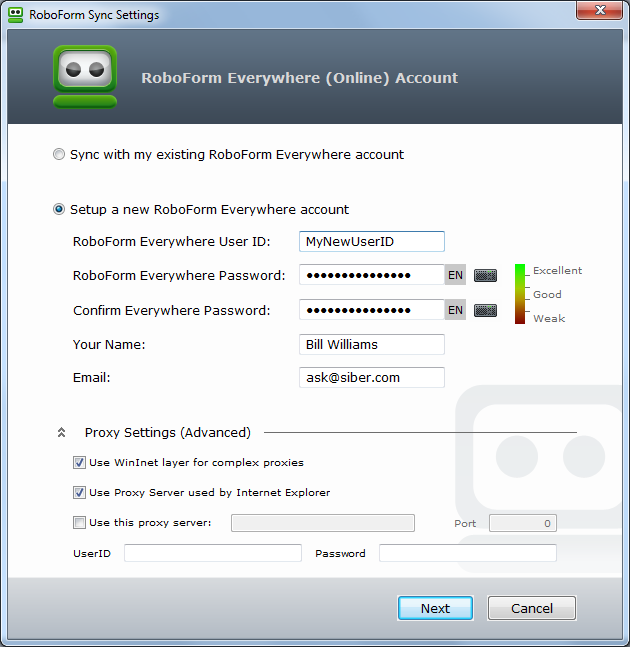
Tutorial: Creating a Master Password Master Password: Password-Protect All Your Files. When RoboForm is installed for the first time you will be asked to create a Master Password. The Master Password will secure your Logins, Identities and Safenotes, ensuring no one will have access to that information unless they enter your Master Password. Master Password Setup If you did not setup your Master Password during the installation, you can set one up at any time. Navigate to Your RoboForm Toolbar.
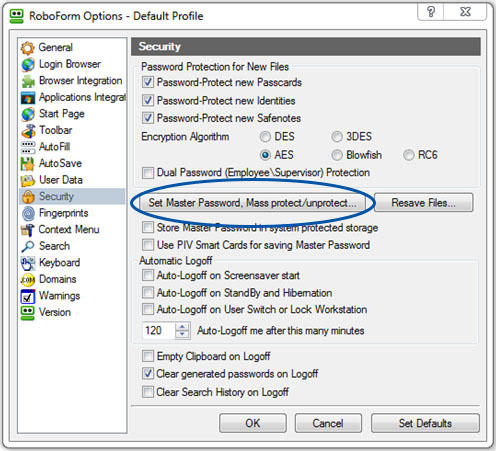
Click on the RoboForm drop down menu. Click on 'Options'. Select 'Security,' then the 'Set Master Password' button.
Create your Master Password. Make sure that all of your New Files are protected by your Master Password by going back to the 'Options' menu and selecting 'Security.' Make sure each box is checked where it says 'Password Protection for New Files.' .
RoboForm offers even more great functionality; feel free to browse our for additional information and a more in-depth look.
Click to expand.Hi D&C, No problem, just a couple of ideas. People usually have passwords that they need to use everyday and then passwords they only need to use rarely.
You could create a master set of Roboform data that would be stored on removeable media (USB/CD/Floppy). This master set would be stored separately from the computer and retrieved only when needed, preferably with a different password (make a backup). Then if your everyday set is compromised by keylogger etc., then you limit the damage. Having your everyday set on removeable media would mean that when the media is removed, then the encrypted passcards, etc. Could not be accessed because they are not physically present. But if you need them every day, you will eventually start to leave the media connected all the time anyway. Having it on removeable media can be very convenient with multiple computers and if you don't need constant access to them, removing the media means the data is physically inaccessible during that time.
I've seen a couple of interesting approaches to passwords. Typically, my passwords will be real sentences with replaced characters.
For example, my online banking password might be $Th3r0bb3rBar0ns007%% (the robber barons with a bit of random fluff at the beginning and at the end because other people letter/symbol substitute too). I'd use this password ONLY for online banking, and I would never write it down. Because there are standard r3plac3m3nts for letters (at least the way I do it) then the password (actually, a passphrase where possible) is memorable, but long.
Of course, individually the words 'The', 'Robber' and 'Barons' are in the dictionary. But the whole concatenated nonsense with extra characters is not. I'll typically also use one password for multiple sites that I don't care about. This is my throwaway password. It's easy to remember, and I don't really care if it's compromised as I don't use it for anything important. I'll have a standard set of variations around it. For example: fastcar fastredcar myfastredcar (using letters, symbols on the end/beginning with subsitution) for example: ^myfa$tr3dcar666# This passphrase means something to me and is therefore easy to remember and slightly modify.
Another system we wrote for a client (an ISP) that wanted to generate passwords generated phonetically memorable, but nonsense words. For example, perfuk69, fneepar765 - these words don't appear in any dictionary I've ever seen and are easily remembered because you can 'pronounce' them. For example, you don't remember 'F N E E P A R 7 6 5' you just remember 'fnee'-'par'765.
It's silly, but it works. Hi Folks: This is one of my fuzzy wuzzy statements that some hate, so to them I say don't read it. If other can say things so can I. If you have Roboform2Go, best to read up how it works.
If you don't have a tool best not to draw conclusions about it til you know. It would be best to re-read Delvico's coments October 12, 1:02AM. I have and use RoboForm2Go daily. It encrypts passwords, uses AES in my version. To access it on the USB stick you have to enter it's PSW by clicking on it's virtual keyboard. So, IF there was a very smart keylogger click tracker operating on your computer that could capture your RoboForm psw whether you are on line or not. The bad guy could wait till you are back on line to do its evil work right?
But all this is speculation. If you rotate your password reguarly that will minimize risk. MINIMIZE does not mean ELIMINATE risk. Get rid of the keylogger would be good as well! If you pratice safe surfing using the tools and advice from this forum, you will minimze risk, but one cannot eliminate it other than by pulling the plug. That's the joy of having an iPod, working as a Hard Drive to store data.
Since my iPod goes wherever I go, most anything that's actually used is on it. Being only a student in High School, I don't have much to actually worry about since I don't have many important things, but what I used to do is have a lot of different passwords, and when I became smarter (sarcasm included), I would just mash my passwords together.
Since most of them were only 6 letters, I could find patterns like 3 of one PW, 3 of Second password, last 3 of first PW, last 3 of second PW, or put them as first letter 1st PW, 1st letter 2nd PW, 2nd letter 1 PW, 2nd letter 2nd PW, and ect. A pretty stupid idea nowadays. Free RoboForm Alternatives Password Management Hi Folks: Here is some data(unverified) posted from the extended list of free utilities. There are 'More great free utilities every month in Support Alert Newsletter' Gizmo Richards service. Just Google it to find. It offers free RoboForm alternatives.
Now we have no reasons left not to do the right thing! ' #71 Best Free Web Form Filler/Password Manager Updated July 25, 2006 Products in this class are among the most useful of all PC utilities because they allow you to complete the common task of filling in web forms and logins by simply clicking a button. They work by saving user IDs, passwords and other information needed for individual sites in encrypted form for later retrieval. To login to a site you only have to type in a single master password to allow retrieval of the specific password information for that site. This information is then used by the program to automatically login. This greatly improves security by allowing different passwords to be assigned to individual sites without the need to be remembered while at the same time making logging in easier and quicker.
School management system project in vb. There's no doubt that RoboForm 1 is the stand-out product in the category; it's full featured, easy to use, seamlessly integrated into both Internet Explorer and FireFox browsers and is constantly being enhanced by the developer. It also allows your saved passwords to be moved between PCs which is very convenient when using multiple machines or upgrading. I do have a major reservation though: The free version allows only 10 forms or passwords to be stored. This used to be 30 in earlier versions which was adequate but 10 is way too few for most users and they will be eventually forced to shell out $29.99 to buy the full product.
This reservation aside, it is a fabulous product that saves me time every day. You'll be amazed how much time it will save you, too. Note: If you use Internet Explorer, there's some good news: the last free version of RoboForm (V5.7.6) that allowed 30 passwords is still available 2 from the RoboForm web site though well hidden in the FAQ. FireFox users are out of luck as you can't use this version with the current FireFox. Some alternatives: First there is the open source program KeePass 3.
It's not nearly as well integrated into your browser as RoboForm but it's a very good product that works without any limitations at all. There's also an excellent KeePass plug-in for Internet Explorer that automates web form filling. Yet another possibility is KeyWallet 4 which is superior to KeePass in the way you can drag and drop saved information directly into web forms. Not quite as neat as RoboForm’s click and fill system but still highly effective. KeyWallet can also automatically save form data, handle difficult Java based forms and is skinable. 1 2 (1.8MB) (Direct download link) 3 (857KB) 4 (1.4MB) '. Ever wondered why when you install windows it makes it difficult to get rid of the U.S character set so you can completely replace it with your own countries one?
Well even MS has difficulty getting through their own backdoors when you do that. Its right what the article says about hashed passwords. In the setup routine of windows you can elect to use say a GB character set but it also insists you keep the U.S one. you have get rid of it twice before moving on to put in a GB character set - then when windows has installed, you unload the U.S character set from in windows as well. Its best to use a non U.S character set for your passwords. Every encryption can be broken - given two things - enough time and enough incentive. Click to expand.
Well time in the case of encryption can also be broken down by how much computer power you throw at the problem. I did say 'given enough time' There are encryptions that are extremely difficult to break such as the method used in PGP - The U.S government had to threaten the inventor of PGP with a long prison term unless he complied with their directives to put in a method by which they can snoop any encrypted message. It is debateable whether he complied with this, therefore the PGP method cannot be trusted.
It is also noteworthy that the U.S government considers encryption to be the privaledge of government, not ordinary citizens and as such deems it to be a threat to national security if they cannot break encryptions run by citizens. Therefore most legit companies will comply with government directives to make their methods known to government (and the pressure is so great they comply usually without a fight). All that information is easily verifiable on the internet. All firewall routing hardware has backdoors for government snoops too - see Cisco, Netgear, all the major manufacturers have followed government orders to do this.
Whether the codes themselves are difficult to break is not the same as saying they cant be broke - over time things move on - thats the job of the NSA - GCHQ etc they are codebreakers with power computers and time My point being that the majority of what passes for unbreakable encryption is undermined by the fact its only unbreakable if you dont have sufficient time, computer power, or position within government hierarchy. Though I am willing to be corrected on that, obviously and if you could show me what you mean by 'If you browse through this forum, you will discover that certain encryption methods cannot be broken in our lifetime' I would be glad to stand corrected. Precisely why I wrote 'debateably' People in the spy business are not averse to double bluff. NSA says put a method so we can snoop - zimmermann says no nsa says ok we drop the case - now the question WHY? Its a noteable point that zimmermann himself came under immense duress to comply. The kind of duress that would cause anyone to buckle at the knees. The fact his source code is out there doesnt imply he's not working with them.
Roboform Everywhere Password Reset
It merely implies you dont know what the NSA or Zimmerman knows. Say hes not working with them and they havent cracked it - well then they may as well give up the business of codebreaking huh? 'Mr president we cant break this code but we sure are working hard at some other stuff less complex' The fact that no USERS of PGP are being brought to trial for failure to release their password is testament - you think terrorists or criminals dont know about PGP? Edited in after about 20 mins Also It strikes me that the creators of such programs will normally have computers interfaced with the net, and their security WHATEVER they use is really going to be no match for any government intent on finding out the secrets they have. As stated in a previous post ALL the manufacturers of security hardware leave open gates for the security services to snoop I suggest you look into the idea of 'port knocking' I believe that is the backdoor method they would use or similar. Ever been hit by a government computer, scanned - look at the port sequences they use!
In Britain it's an offense punishable by two years in jail to withold an encryption key from the authorities. Telling someone the authorities have made such a request is punishable by 5 years in jail. The Regulation of Investigatory Powers Bill (RIP) will be presented to the Commons for the final reading Wednesday after amendments made in the House of Lords. The RIP legislation requires Internet Service Providers (ISPs) to install a so-called “black box” device allowing access by the security forces to email messages hosted on an ISP's computers. The black box will transfer data over secure channels to a new Government Technical Assistance Centre, which is to be built at a cost of billions of pounds. The RIP bill also gives police the power to demand that those whose email is intercepted hand over any software keys and passwords necessary to read encrypted mail.
Failure to do so could result in two years imprisonment. Telling a third party that such a request has been made carries a possible five-year sentence.
As with other law-and-order measures introduced by the Blair government, the draconian legislation has been justified on the grounds of thwarting “terrorists”, “paedophiles” and “organised crime”. Tucked away in part five of the proposed bill, however, in a section titled Supplemental, one finds a staggering indication of both the scope of the new powers and the legislation's real purpose. Dealing with the “general interpretation” of the proposed law, the document explains that “serious crime” refers to crimes that satisfy two tests. The first is that the offence would carry a prison sentence of more than three years for anyone over 21 years of age. The second reads as follows: “That the conduct involved the use of violence, results in substantial financial gain or is conducted by a large number of persons in pursuit of a common purpose” (emphasis added). In September 2003, Home Secretary David Blunkett announced wide-ranging extensions to the list of those entitled to see information collected under the RIPA. The list now includes jobcentres, local councils, and the Chief Inspector of Schools.